What Top-level Domains attract Phishers?
Contributed by Dave Piscitello, Interisle Consulting Group
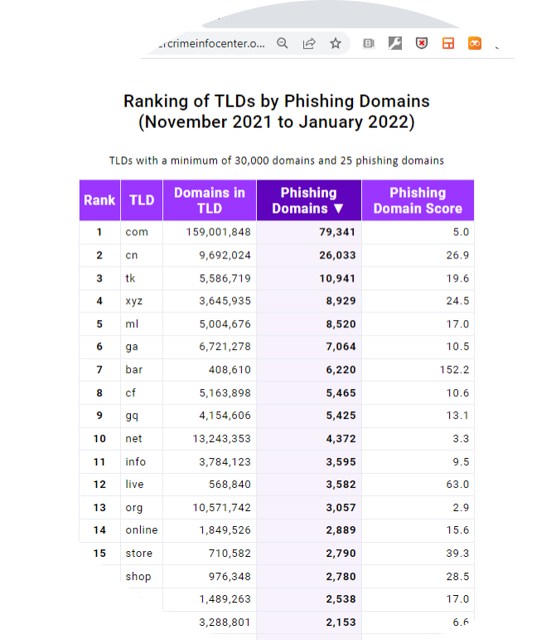
The Cybercrime Information Center publishes quarterly updates of phishing activity. These updates include tables of the Top-level Domains where phishing activity is reported. The tables report the 20 Top-level Domains that have the most reported phishing domains, ranked by domain count and by a metric, phishing score. The Center also publishes phishing activity table data containing the reported phishing domains for all of the Top-level domains with a minimum of 30,000 domains and 25 phishing domains.
In this post, we demonstrate how you can use the Cybercrime Information Center’s quarterly phishing activity table data to study which Top-level Domains criminals are using for domain names that they purposely register for phishing. We call these malicious domain registrations.
Distinguishing malicious phishing domains from compromised web sites where phishing pages are hosted without authorization is a useful distinction for phishing mitigation (e.g., takedowns) and to identify parties whose processes or practices make them vulnerable to abuse.
Download a CIC TLD data file
Go to the Cybercrime Information Center’s Records Repository at https://www.cybercrimeinfocenter.org/records.
Select the TLD Phishing Table Data from the November 2021 – January 2022 pulldown menu to download the file phishing-tldstatsNov2021-Jan2022.csv.
Run Excel
When the download completes, Open the file phishing-tldstatsNov2021-Jan2022.csv. If you don’t see the file, check that you are looking for All Files (*.*).
For this demonstration, we use the Hide feature in Excel. First, select Columns C-H and then choose Hide from the dropdown menu.
Now we can focus on the columns that contain malicious phishing domain registrations data. With columns C-H hidden, your worksheet should look like this:
Next, we prepare to apply filters. Use the shortcut key, Ctrl+A, to select the entire worksheet. Then, from the Data pulldown, select Filter. This enables filters for all columns.
Choose Column G, Malicious Phishing Domains. From the ▽ pulldown choose Sort Largest to Smallest (If not the default, choose Expand the Selection). Now apply a Number filter to Column I; here, choose Greater Than Or Equal To and set the value to 500. The spreadsheet now ranks the Top-level Domains that have 500 or more reported Malicious Phishing Domains.
For this quarter, 28 TLDs had more than 500 malicious phishing domain registrations. To continue the demonstration, let’s look at ccTLDs separately from gTLDs.
What ccTLDs attract phishers?
To see only ccTLDs, we’ll use a text filter. Select column A, TLD. Next, choose Text Filters -> Equals from the ▽ pulldown. Type ?? into the Custom Autofilter and hit OK. You should now see only the 10 ccTLDs with 500 or more malicious phishing domain registrations in your worksheet.
Column A now shows ccTLDs sorted by a count of Malicious Phishing Domains.
Column B shows the approximate number or domains delegated from the ccTLD (DUM, or domains under management). We (or you) can use this to calculate percentages of malicious phishing domain registrations for each TLD.
The 10 ccTLDs with the highest counts of phishing domains for this reporting period were: .TK, .ML, .GA, .CF, .GQ, .CN, .US, .RU, .PW, and .CO. You can repeat this exercise with TLD table data for any prior or future quarter reported at the Cybercrime Information Center. Five of these ccTLDs - in fact, the top five - are “commercialized” ccTLDs run by Freenom which offers free domain name registrations.
What gTLDs attract phishers?
To see only gTLDs, we’ll reverse the text filter. Select column A, TLD. Next, choose Text Filters -> Does Not Equal from the ▽ pulldown. Type ?? into the Custom Autofilter and hit OK. You now have the 17 gTLDs with 500 or more malicious phishing domain registrations. I’ve added a color background to Column A cells to distinguish the “legacy” TLDs (delegated prior to 2012) and “new TLDs” (delegated after 2012) in yellow and orange, respectively.
The Phishing TLD Table data also contains a Malicious Phishing Domains Score in Column J, which is determined by dividing the number of malicious phishing domains by the “number of domain names delegated from a TLD multiplied by 10,000”. This score allows us to compare very large TLDs like .com against smaller ones like .BAR or .VIP without a size bias.
Using the Excel MEDIAN function, we determined that the median malicious phishing domain score for gTLDs in this quarter was 17.87. The 16 gTLDs that exceed the median, all new TLDs, are shown in the table below.
Interisle studies phishing trends over time - for example, we identify TLDs that are repeatedly abused by phishers and we look for flocking or migration patterns among TLDs. You can use the filters and sorts we demonstrated here on other quarterly CIC phishing table data to look at sets of TLDs that interest you, for example, a set of regional ccTLDs (e.g., Asia-Pacific or EU) or new TLDs that were assigned by ICANN to a single registry operator.
Closing remarks
If you apply other filter or sorts to the Phishing TLD Table data, you can learn a great deal more about the TLDs that are abused for phishing. For example,
.COM has the highest raw counts of malicious phishing domains (47,129) among all gTLDs but, relative to other gTLDs with a minimum of 30,000 domains and 25 phishing domains, its malicious phishing domain score of 2.96 is low.
The median gTLD malicious phishing domain score is nearly six times that of .com.
Sixteen (16) new TLDs exceed the median gTLD malicious phishing domain score.
The median malicious phishing domain score for ccTLDs with a minimum of 30,000 domains and 25 phishing domains is only 0.15, but the median score for the “commercialized” ccTLDs run by Freenom is 13.06.
These examples show how measurements can shape questions for policy makers or legislators; for example,
What practices or policies make one TLD more attractive than others to phishers?
What ccTLD policies or practices contribute to low malicious phishing domain registrations numbers and scores?
What Freenom policies make .TK, .ML, .GA, .CF, and .GQ so attractive to phishers?
If you have a novel use for Cybercrime Information Center Data and are interested in sharing with
our community, contact us at
criminaldomainabuse@interisle.net